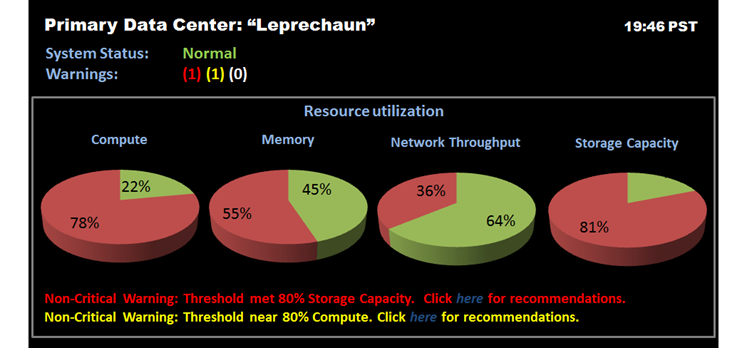
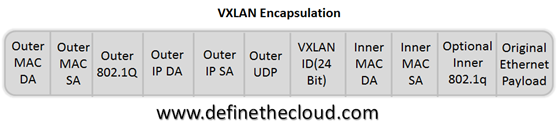
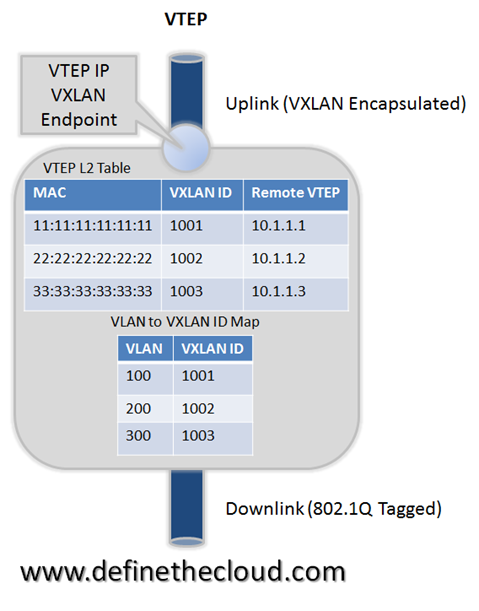
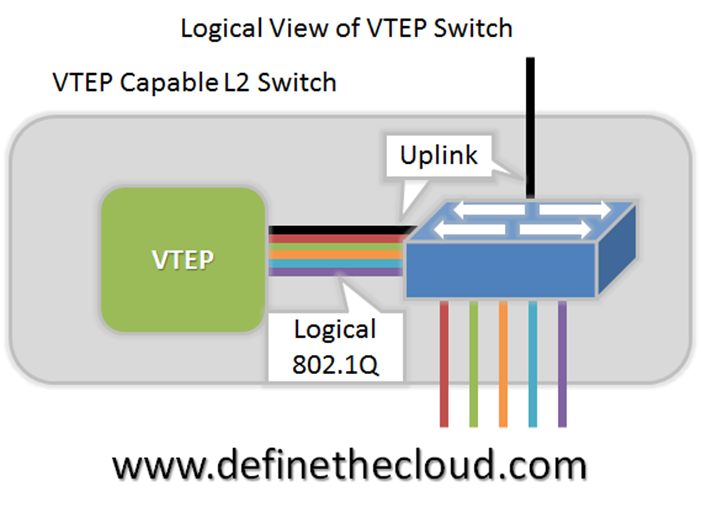
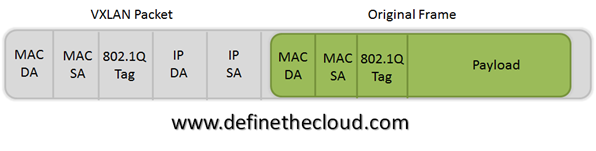
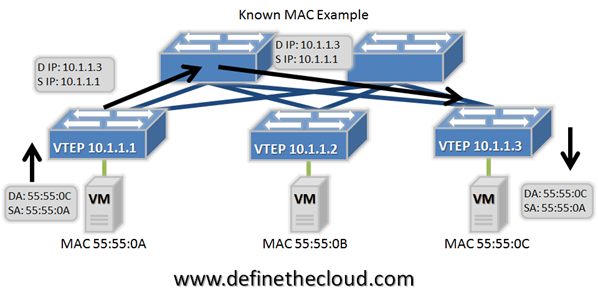
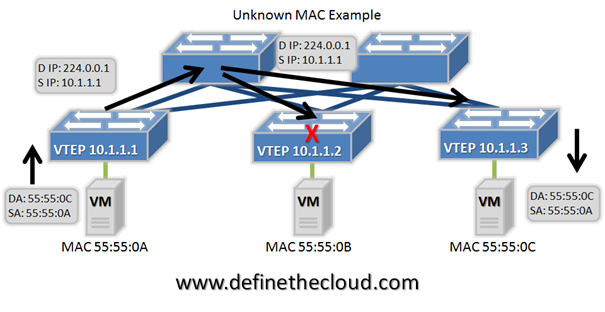
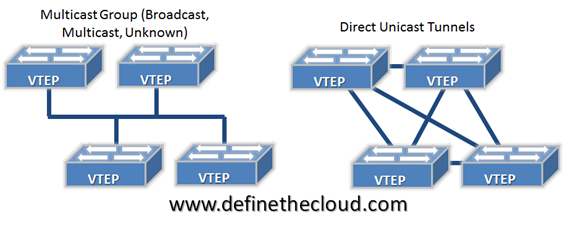
Cisco has announced the reworking of its
cloud provider and reseller programs, and its Managed Services program, merging
them into a single united program.
"Every analyst confirms that the cloud is only becoming bigger, with IDC
forecasting nearly 30% of all IT will be in the cloud by 2020," said Ricardo
Moreno, Senior. Director, Channels Programs & Strategy at Cisco.
"It's huge
and it's there for partners to capture the opportunity."
Moreno acknowledged the new program represents a significant rethink of how
Cisco is approaching the cloud.
"Since two years ago, when we came up with the strategy, our Go-to-Market
strategy has been partner based," Moreno said.
"We have learned from our
original programs and are evolving them now."
Cisco's cloud strategy -- in common with several other vendors -- defines
three key roles for partners: cloud builder; cloud provider and cloud reseller. The cloud builder role, which Moreno said was closest to the traditional
integration business, was evolved in September into the Master Cloud Builder
specialization.
"The idea was to leverage the model that the partners know best, and we added
some elements including application knowledge to the Cloud Builder
specialization," Moreno said.
"Now, with this new announcement the cloud provider and reseller roles are
being combined with the Managed Services program which we have had in place for
six years into a new Cloud and Managed Services portfolio," Moreno said.
"There is much greater simplification from turning two program tracks into a
simple program," Moreno said.
These include streamlined audits and simplified
pricing. The pricing will be consistent and predictable globally, allowing
partners to position and sell Cisco-Powered managed and cloud services more
effectively.
Rebates have also been enhanced. CMSP partners can take advantage of the
Cisco Value Incentive Program (VIP), effective January 27, 2013.
This replaces
the current Cisco Managed Services Channel Program (MSCP) rebates.
"Cloud providers before did not have access to rebates, and neither they nor
managed service providers has had access to VIP through that program," Moreno
said.
"This makes one single rebate process to manage. The previous program had
some flat rebates and now they have all been enhanced and harmonized."
CMSP partners are also eligible for additional Cisco incentive programs
including Opportunity Incentive Program (OIP), Teaming Incentive Program (TIP),
Solution Incentive Program (SIP), and Technology Migration Program (TMP).
"In the past, all these were not available to these partners," Moreno said.
In addition, "Cisco Powered" branding will be a part of CMSP, to provide
partners with strong branding.
"This is something we hadn't been promoting in recent years in managed
services, but we will be now," Moreno said.
Once certified, CMSP partners can now sell and deliver cloud & managed
services globally.
"Being able to offer services outside of their region without qualifying
again is important for cloud partners," Moreno said.
Finally, to assist partners in building, marketing, and selling their
services, Cloud Market Development Funds, business acceleration tools and
services, sales training and Cisco's Cloud Marketplace
(http://marketplace.cisco.com/cloud) will be available.
"Any CMSP participant can advertise themselves on Cisco Cloud Marketplace to
other partners," Moreno said. "This promotes partner to partner collaboration.
This was announced in September, but very much connects to what we are doing
here."
The transition process will last until August 1, 2013, after which the old
MSCP managed services program will disappear,
"That should be ample time to transition -- 9 to 23 months depending on the
anniversary date," Moreno said.
The biggest change in qualification requirements will be that under the CMSP,
Cisco Powered Service designations are being elevated to mandatory requirements.
"There are two main changes," said Arjun Lahiri, Senior Manager, Worldwide
Channels at Cisco.
"CMSP Master partners will need to have a minimum of two
Cisco Powered Services, and CMSP Advanced Partners will be required to have one.
Today, these are not mandates, but with the new program they will be mandatory."
The CMSP Express partner tier will not be required to qualify on any Cisco
Powered Services, but Lahiri said they will be required to have two Cisco-based
services, with the difference being that these may have some other vendor
equipment, while the Cisco Powered services are exclusively Cisco validated and
tested.